Image 1 of 4
Image 1 of 4

 Image 2 of 4
Image 2 of 4

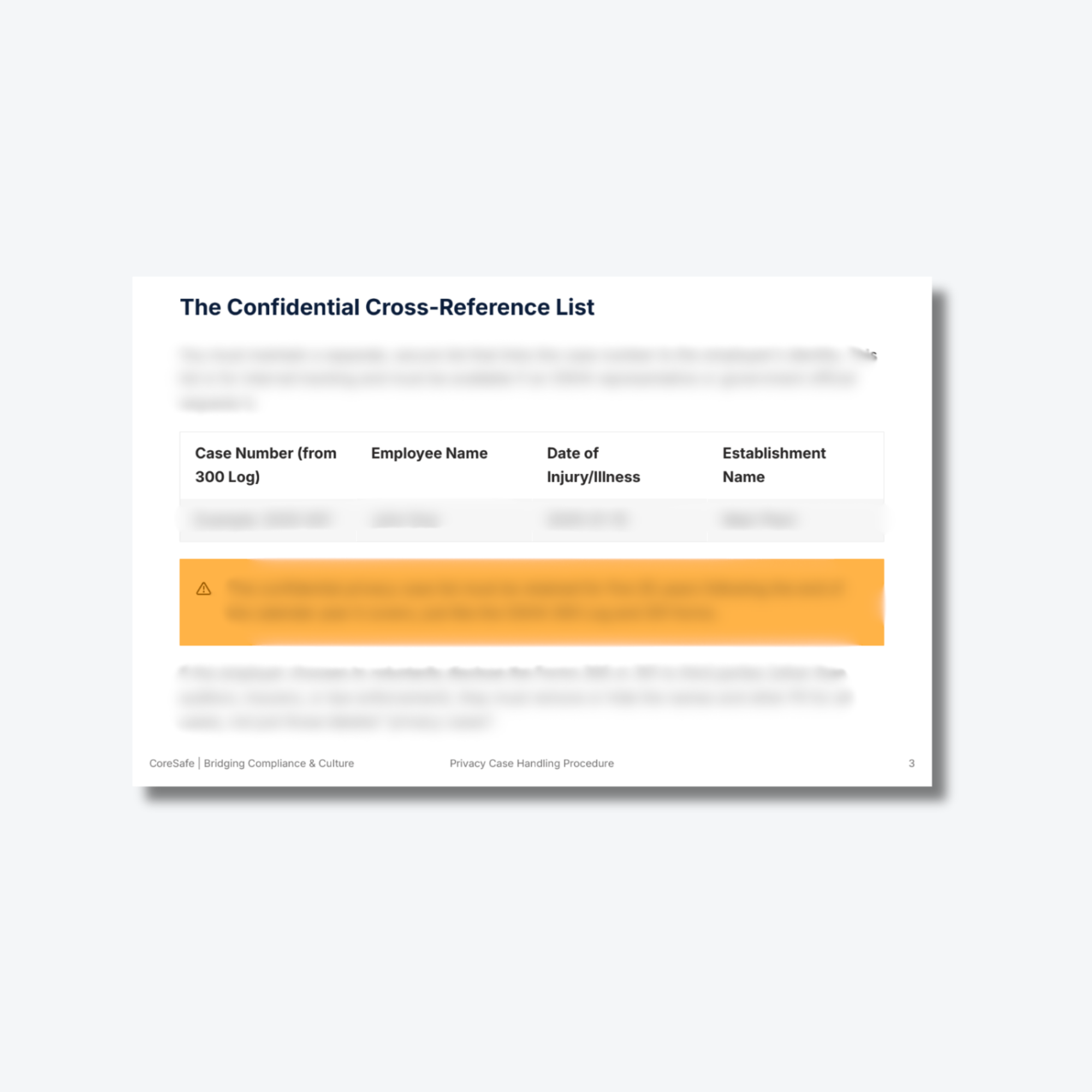 Image 3 of 4
Image 3 of 4

 Image 4 of 4
Image 4 of 4





Privacy Case Documentation Worksheet – Protect Employee Dignity and Maintain Recordkeeping Compliance
This Is for You If...
You are a System Builder standardizing sensitive recordkeeping procedures across multiple departments to ensure consistent, professional documentation.
You are a Culture Leader strengthening employee trust by protecting personal health information while maintaining transparent safety records.
You are preparing for an OSHA audit and need a defensible framework for identifying and recording privacy-specific cases.
You want to eliminate confusion regarding 1904.29(b)(7) requirements to avoid exposing intimate details or facing non-compliance penalties.
What's Inside
A comprehensive 5-page training guide covering complex recordkeeping requirements for IMMEDIATE deployment across your safety program to ensure regulatory alignment and privacy:
Privacy Case Identification Matrix: Clear criteria for identifying the six mandatory categories including intimate body parts, mental illness, and contaminated sharps.
OSHA 300 Logging Procedure: Detailed instructions for omitting names and using correct labels to maintain a compliant and professional Log 300.
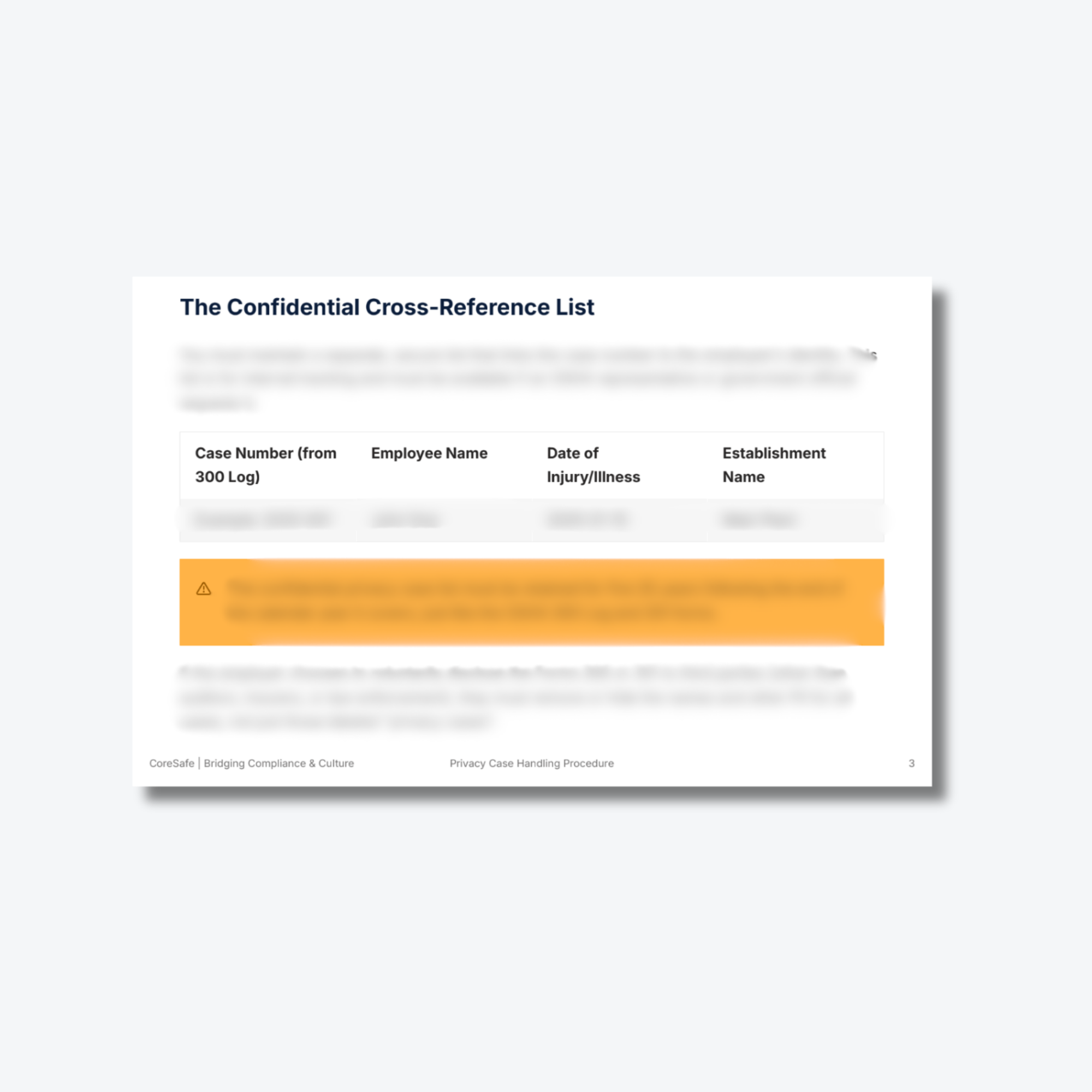
Confidential Cross-Reference List: A secure internal tracking template used to link case numbers to employee identities for authorized government review.
Prohibited vs. Approved Description Framework: Practical examples for rewriting sensitive incident descriptions to remove intimate details while keeping the work-related cause clear.
Privacy Case Determination Checklist: Three essential questions to verify category alignment, professional language, and file security before recording sensitive data.
Employee Request Processing Protocol: A three-step verification and documentation workflow for handling voluntary employee requests to keep specific illnesses private.
How It Helps You Today
✅ Defensibility: Provides a structured, regulatory-aligned framework for recording sensitive cases that meets rigorous OSHA 1904 recordkeeping expectations.
✅ Eliminates Decision Fatigue: Simplifies complex privacy determinations with clear checklists and approved description examples that remove professional guesswork.
✅ Saves Critical Time: Delivers ready-to-use protocols and tracking templates that eliminate the need to research and build privacy workflows.
Bridge the gap between compliance and culture with defensible, ready-to-use documentation.
This Is for You If...
You are a System Builder standardizing sensitive recordkeeping procedures across multiple departments to ensure consistent, professional documentation.
You are a Culture Leader strengthening employee trust by protecting personal health information while maintaining transparent safety records.
You are preparing for an OSHA audit and need a defensible framework for identifying and recording privacy-specific cases.
You want to eliminate confusion regarding 1904.29(b)(7) requirements to avoid exposing intimate details or facing non-compliance penalties.
What's Inside
A comprehensive 5-page training guide covering complex recordkeeping requirements for IMMEDIATE deployment across your safety program to ensure regulatory alignment and privacy:
Privacy Case Identification Matrix: Clear criteria for identifying the six mandatory categories including intimate body parts, mental illness, and contaminated sharps.
OSHA 300 Logging Procedure: Detailed instructions for omitting names and using correct labels to maintain a compliant and professional Log 300.
Confidential Cross-Reference List: A secure internal tracking template used to link case numbers to employee identities for authorized government review.
Prohibited vs. Approved Description Framework: Practical examples for rewriting sensitive incident descriptions to remove intimate details while keeping the work-related cause clear.
Privacy Case Determination Checklist: Three essential questions to verify category alignment, professional language, and file security before recording sensitive data.
Employee Request Processing Protocol: A three-step verification and documentation workflow for handling voluntary employee requests to keep specific illnesses private.
How It Helps You Today
✅ Defensibility: Provides a structured, regulatory-aligned framework for recording sensitive cases that meets rigorous OSHA 1904 recordkeeping expectations.
✅ Eliminates Decision Fatigue: Simplifies complex privacy determinations with clear checklists and approved description examples that remove professional guesswork.
✅ Saves Critical Time: Delivers ready-to-use protocols and tracking templates that eliminate the need to research and build privacy workflows.
Bridge the gap between compliance and culture with defensible, ready-to-use documentation.
FILE FORMATS & DELIVERY
This toolkit includes one PDF document delivered as an instant digital download. All files are delivered via email immediately after purchase.
CUSTOMIZATION & USAGE RIGHTS
PDF guides are reference-only. You may use these materials across your organization without additional licensing fees to train your management team and standardize recordkeeping.
FREQUENTLY ASKED QUESTIONS
Can I use this across multiple sites?
Yes. Your purchase grants unlimited internal use across all locations within your organization.
Does this guarantee compliance?
These tools are designed to support defensible documentation aligned with OSHA expectations under 29 CFR 1904.29. CoreSafe does not provide legal advice or guarantee regulatory compliance.
How quickly can I deploy this?
Immediately. All files are ready-to-use upon download and require minimal customization to integrate into your existing safety management system.
Do you offer refunds?
Due to the digital nature of these products, all sales are final. If you have questions about fit or content before purchasing, contact info@coresafe.org.
REGULATORY ALIGNMENT
This toolkit reflects current OSHA recordkeeping requirements under 29 CFR 1904.29(b)(6) through 1904.29(b)(10) and incorporates best practices for protecting Personally Identifiable Information (PII).